Overview
This guide walks you through creating an OAuth application in Microsoft Entra ID for use with Airia. This enables secure integration with Microsoft 365 Tools including Outlook, Teams, OneDrive, SharePoint, and the Graph MCP Server.Prerequisites
Before you begin, ensure you have:- Azure admin access - You need permissions to register applications in Azure AD
- Active Azure/Microsoft 365 subscription - Your organization’s Azure tenant
- Airia callback URL - Available in the Airia platform OAuth configuration page
If you don’t have permission to register applications in Azure AD, contact your IT administrator to either grant you the necessary permissions or complete this setup on your behalf.
Step 1: Access the Azure Portal
- Navigate to the Azure Portal
- Sign in with your organizational account that has admin privileges
- In the search bar at the top, type “Microsoft Entra ID” or “Azure Active Directory”
- Select Microsoft Entra ID from the results
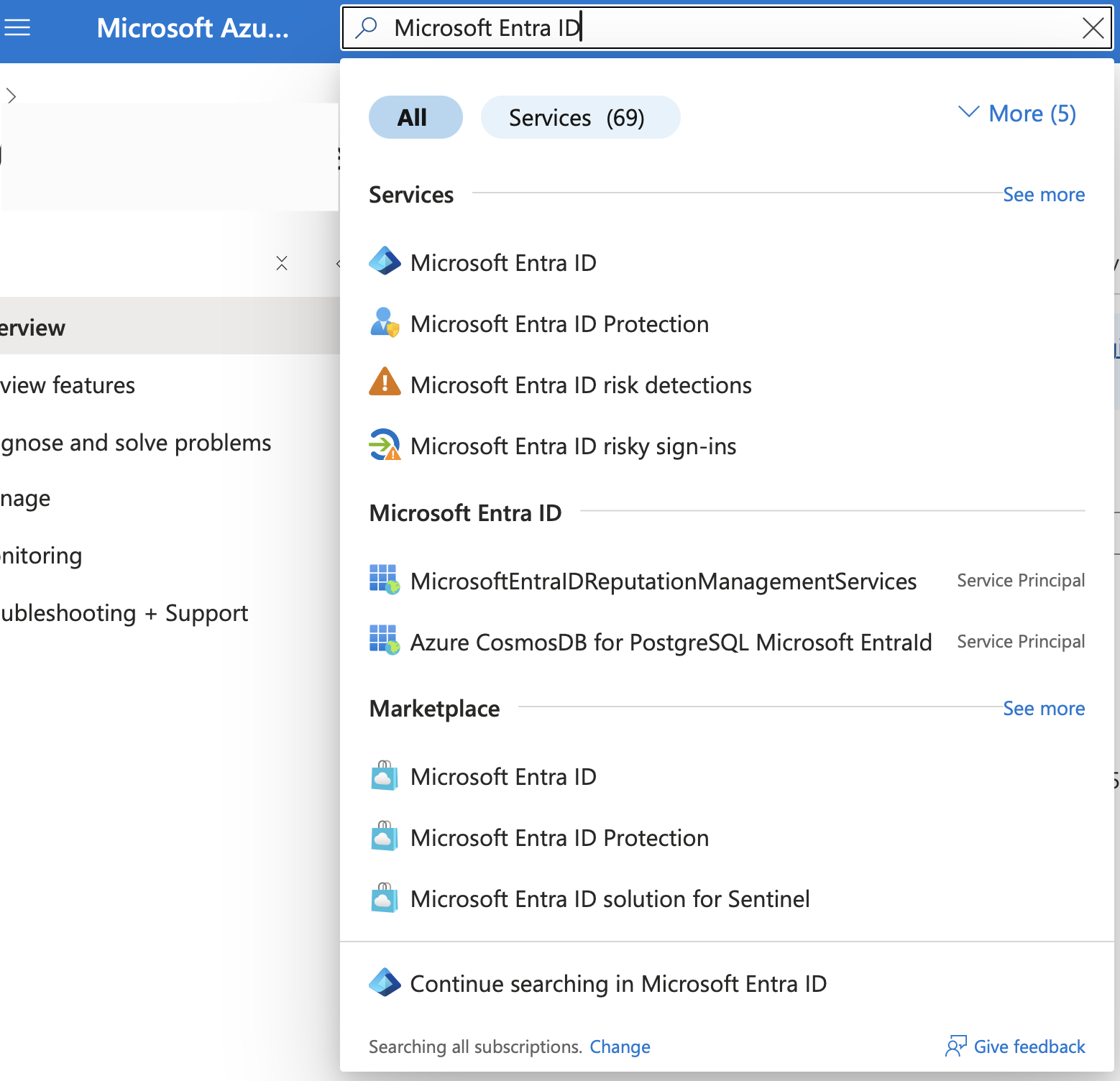
If your organization uses multiple Azure tenants, ensure you’re in the correct tenant by checking the directory name in the top-right corner of the portal.
Step 2: Register a New Application
- In the Microsoft Entra ID overview page, look for Manage in the left sidebar
- Click on App registrations
- Click the + New registration button at the top
Step 3: Configure Application Registration
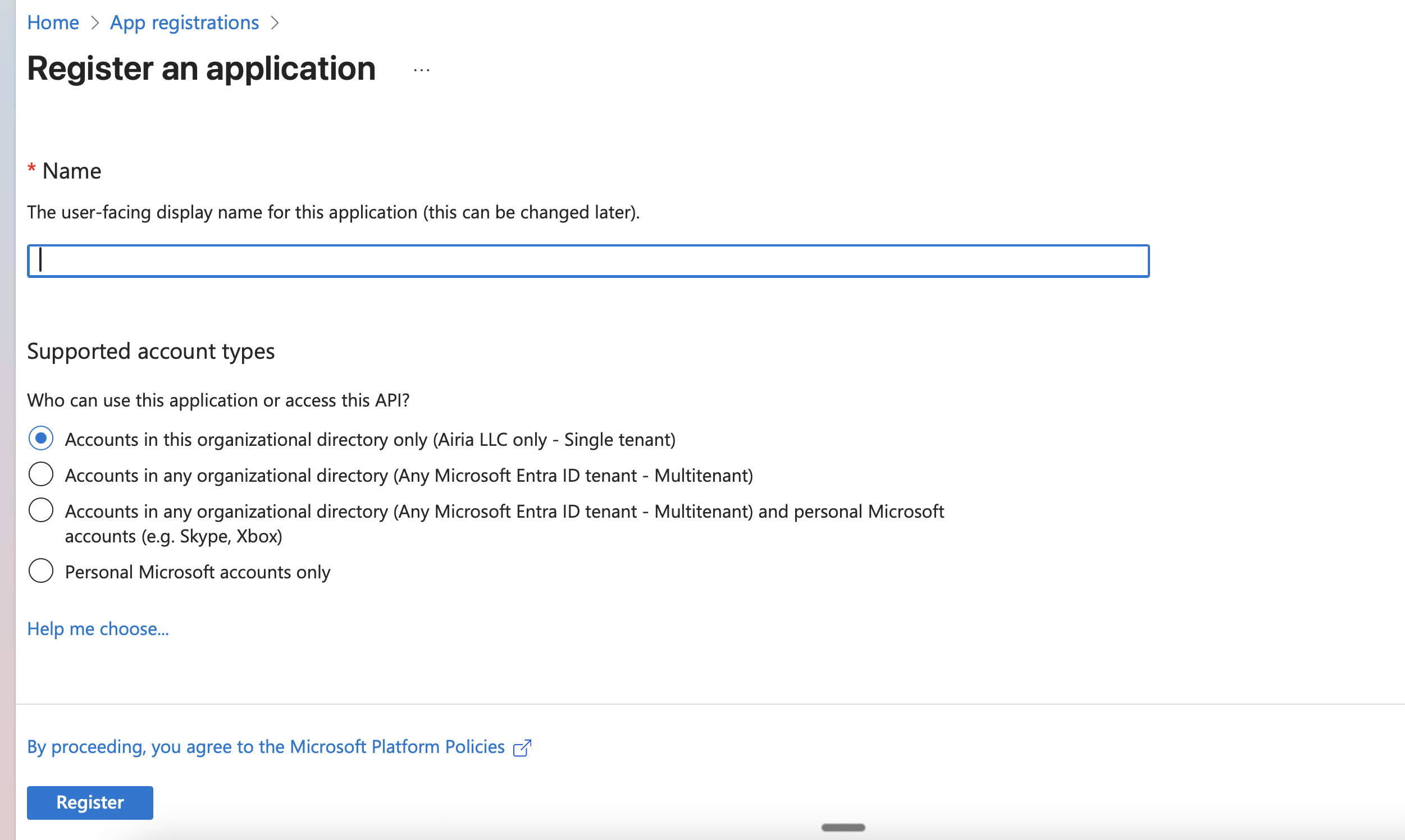
Fill out the application registration form:Basic Information
-
Name: Enter a descriptive name for your application
- Example:
Airia OAuth IntegrationorAiria - Microsoft Services - This name will be visible to users during the consent process
- Example:
-
Supported account types: Choose based on your needs
- Recommended: “Accounts in this organizational directory only (Single tenant)”
- This is more secure and appropriate for most enterprise use cases
-
Redirect URI:
- Select Web from the dropdown
- Enter your Airia callback URL(s) as shown on the OAuth configuration page
- Click Register to create the application
Step 4: Copy Your Application (Client) ID
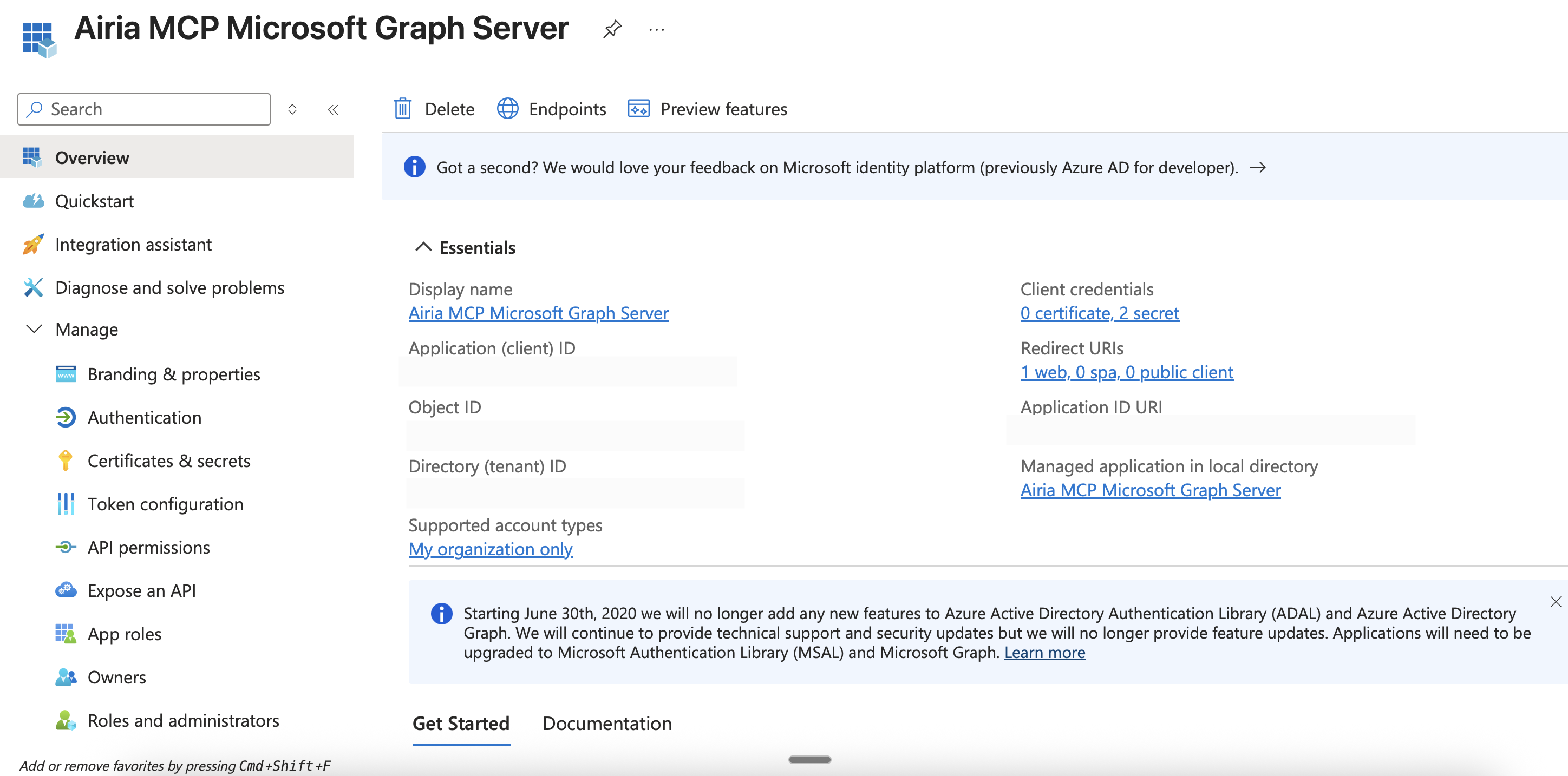
- In the left sidebar, click on Overview
- You’ll see the Application (client) ID prominently displayed
- Click the copy icon next to the Client ID to copy it
- Save this ID - you’ll need it for Airia configuration
The Application (client) ID is a public identifier and is safe to share within your organization. However, keep track of where you paste it.
Step 6: Generate a Client Secret
- In the left sidebar under Manage, click Certificates & secrets
- Click on the Client secrets tab
- Click + New client secret
-
In the dialog that appears:
- Description: Enter a meaningful description (e.g., “Airia OAuth Integration”)
- Click Add
Step 7: Configure API Permissions
Now you’ll configure which Microsoft Graph APIs your application can access.- In the left sidebar under Manage, click API permissions
- You’ll see Microsoft Graph → User.Read is already added by default
- Click + Add a permission
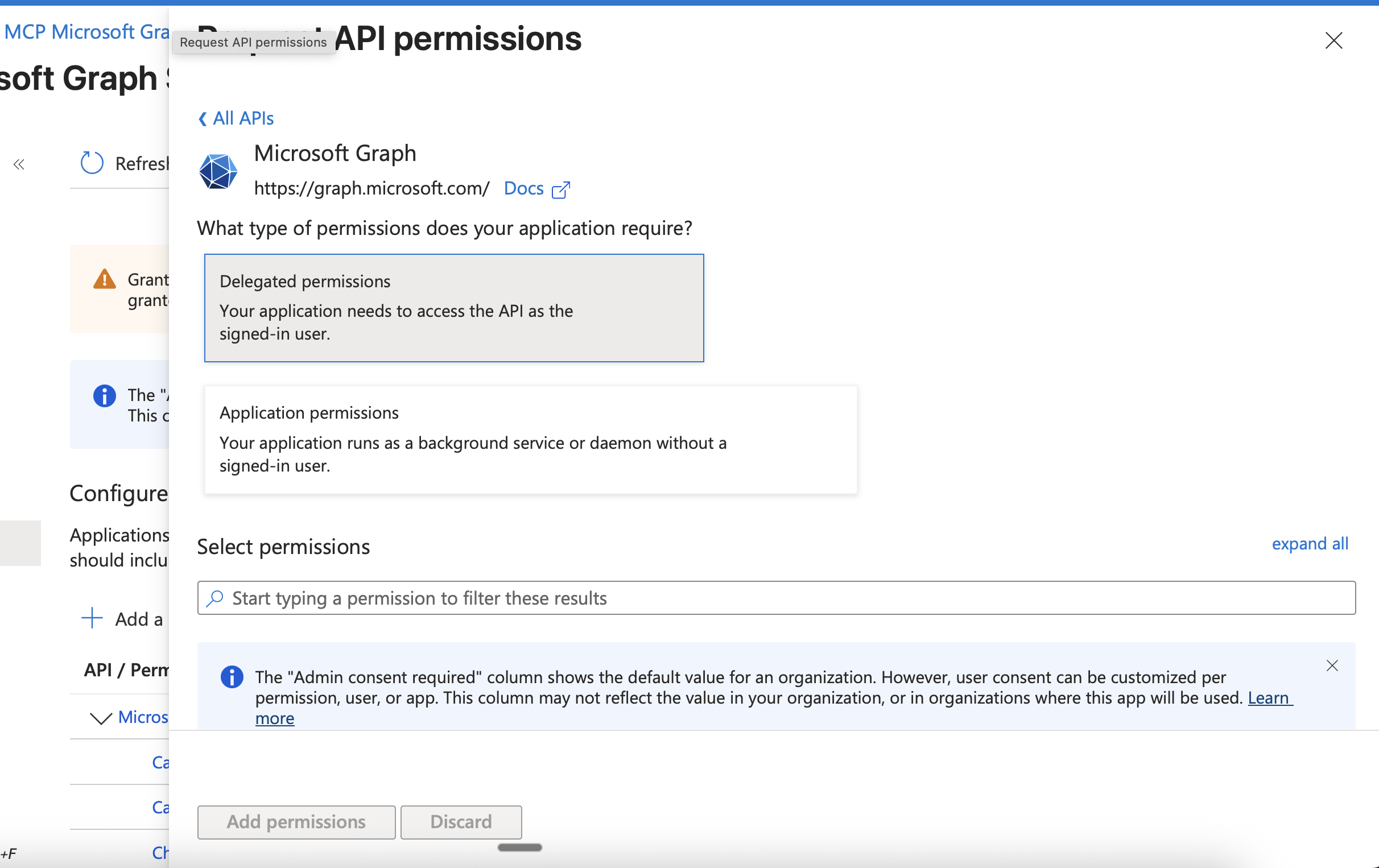
- Select Microsoft Graph
- Choose Delegated permissions (not Application permissions)
Required Permissions
Add the following delegated permissions by searching for each one and checking its checkbox:Mail Permissions
Mail.Read- Read user mailMail.Read.Shared- Read mail in shared foldersMail.ReadWrite- Read and write user mailMail.Send- Send mail as a user
Calendar Permissions
Calendars.Read- Read user calendarsCalendars.Read.Shared- Read shared calendarsCalendars.ReadWrite- Read and write user calendars
Contacts Permissions
Contacts.Read- Read user contactsContacts.ReadWrite- Read and write user contacts
Files & SharePoint Permissions
Files.Read- Read user filesFiles.Read.All- Read all files user can accessFiles.ReadWrite- Read and write user filesSites.Read.All- Read items in all site collections
Teams Permissions
Team.ReadBasic.All- Read the names and descriptions of teamsChannel.ReadBasic.All- Read channel names and descriptionsChannelMessage.Send- Send messages in channels
OneNote Permissions
Notes.Read- Read user OneNote notebooksNotes.ReadWrite- Read and write user OneNote notebooksNotes.Create- Create user OneNote notebooks
User & Directory Permissions
User.Read- Sign in and read user profile (already added)User.Read.All- Read all users’ basic profilesPeople.Read- Read users’ relevant people listsPresence.Read- Read user’s presence informationGroup.Read.All- Read all groupsDirectory.Read.All- Read directory data
Tasks Permissions
Tasks.Read- Read user tasksTasks.ReadWrite- Create, read, update and delete user tasks
Essential Permissions
email- View users’ email addressopenid- Sign users inoffline_access- Maintain access to data you have given it access to
About Permission ScopesThese are the recommended scopes that Airia uses by default. You can:
- Add more permissions if you need additional functionality
- Remove permissions that you don’t need (though this may limit Airia functionality)
- Add permissions later if you discover you need them
- After adding all permissions, click Add permissions at the bottom
- You’ll see all permissions listed on the API permissions page
Step 8: Grant Admin Consent
Some of the permissions you add may require administrator consent before users can use them.- On the API permissions page, review your added permissions
- Look for the Status column - you may see “Not granted for [Your Organization]”
- Click the Grant admin consent for [Your Organization] button
- In the confirmation dialog, click Yes
- After granting consent, the Status column should show green checkmarks with “Granted for [Your Organization]”
Step 9: Gather Your OAuth Credentials
You now have everything you need to configure Airia. Gather the following information:| Credential | Where to Find It | Example |
|---|---|---|
| Client ID | Overview page → Application (client) ID | 12345678-1234-1234-1234-123456789abc |
| Client Secret | The value you copied when creating the secret | abc123XYZ~... |
| Tenant ID (optional) | Overview page → Directory (tenant) ID | 87654321-4321-4321-4321-987654321xyz |
About Tenant IDFor single-tenant applications, you may need the Tenant ID for certain configurations. It’s displayed on the Overview page. Copy it for reference even if not immediately needed.
Step 10: Configure OAuth in Airia
Now you’ll enter these credentials into the Airia platform:- Log in to your Airia platform
- Navigate to Settings → Integrations → OAuth Connectorsn
- Select Microsoft as the provider
- Enter your credentials:
- Client ID: Paste the Application (client) ID
- Client Secret: Paste the client secret value
- Tenant ID: (if required) Paste the Directory (tenant) ID
- The callback URL should be pre-filled and visible on the configuration page. This should default to
https://auth.airia.ai/OAuth/callback - Click Save or Connect

Step 11: Test the Connection
- After saving, click Connect Account in Airia
- You’ll be redirected to Microsoft’s login page
- Sign in with your Microsoft account
- Review the permissions consent screen
- Click Accept to grant permissions
- You should be redirected back to Airia with a success message
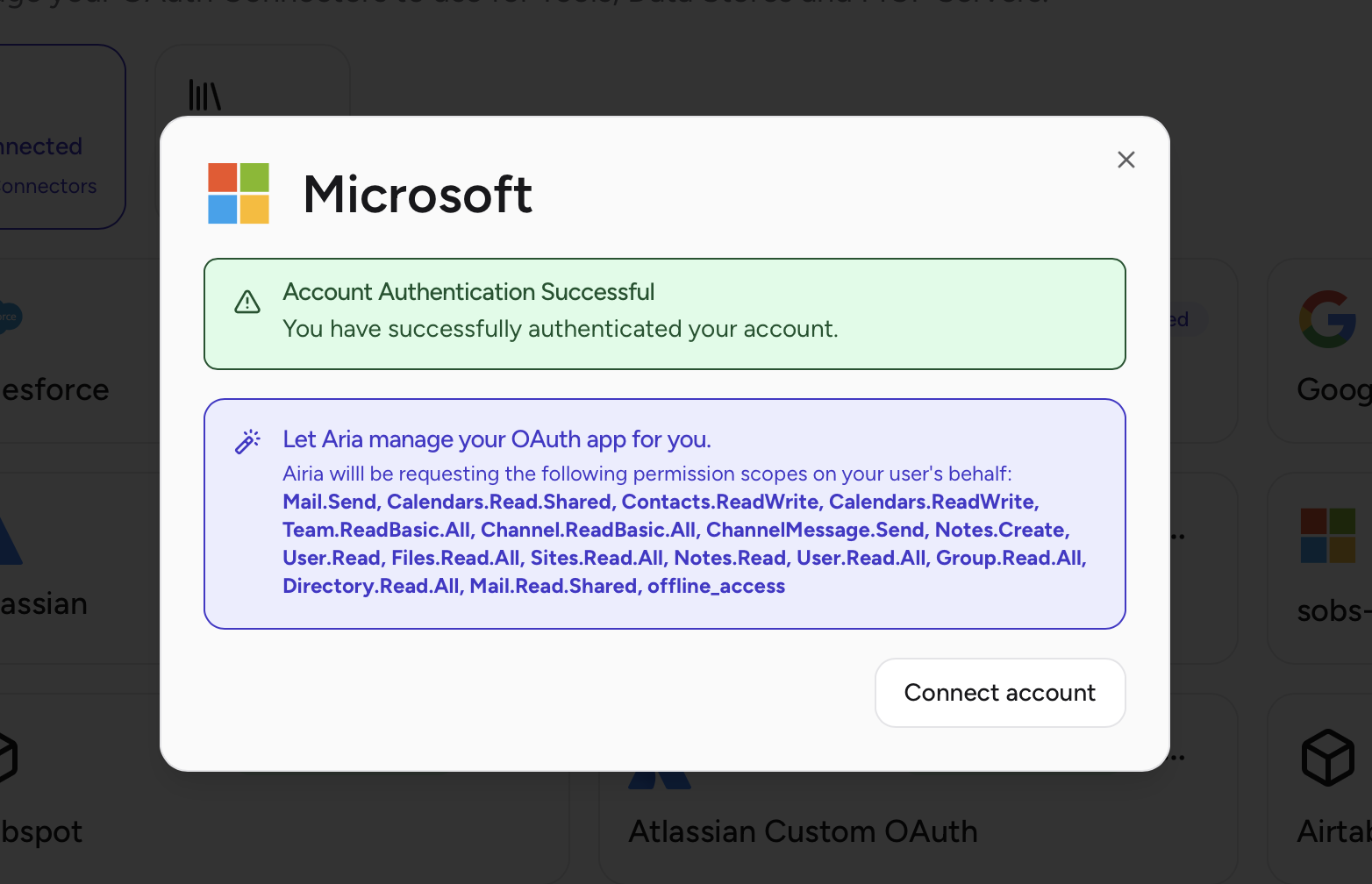
First-Time AuthenticationThe first user to authenticate will see the full consent screen listing all permissions. Subsequent users (after admin consent) will have a simplified experience.
Additional Resources
Need help? Contact Airia support or your IT administrator for assistance with Microsoft Entra ID configuration.
